Reporting from DEF2015: The implications of the Code as Law
View all news items16 April 2015

In March 2015, I was a speaker at the Digital Enlightenment forum 2015 (DEF2015). This blog is focused on a specific talk from this forum: Legal questions in the digital world by TJ McIntyre – UCD and Digital rights Ireland. The event talks and presentations can be found HERE.
The discussion related to the loss of Utopian ideals on which the Internet has been founded – specifically in the legally murky world of ‘Code as law’ – which encapsulates legal enforcement in the form of Code. “Code as law” also creates a new (often reluctant) law enforcer in the form of ICT companies. This issue is thus a key part of Internet Governance today. The blog presents my views on this talk (I am playing a reporting function).
Analysis
No matter which side of the argument you are on, the talk raises some important issues especially in relation to Internet governance. For the most part, this blog simply reports on the issue of ‘code as law’ from the talk. The issue is crucial to Internet governance because Internet governance is being handled by proxy through Code.
There was a comment in the discussion that the talk seems to be making a case for ‘more lawyers’, the implication being that no one really likes more lawyers. However, the option (which seems to prevail today) is worse because we see regulation by proxy by entities that do not have a legal mandate. These entities have to implement the “code as law” but are often reluctant to undertake a policing role.
Over time, this will have profound implications. It is a wider trend of Balkanizing the internet, and the courts have yet to fully confront these issues. We must not let fundamental values of rule of law be lost in a move towards technological enforcement
Code as law and implications of co-regulation for Internet Governance
The Utopian world of the Internet can be summarized with this 1996 quote
“The real issue is control. The Internet is too widespread to be easily dominated by any single government. By creating a seamless global-economic zone, borderless and unregulatable, the Internet calls into question the very idea of a nation-state.” John Perry Barlow, “Thinking locally, acting globally.”
In 2015, that vision has been largely lost – which means that the traditional nation states have indeed found both reasons and ways to regulate the Internet “at the border”.
Three strategies could be potentially used to manage the Internet
1) Internet architecture could be remade
2) Gatekeepers (ISPs, email providers) could be enlisted
3) Self-regulation could be harnessed by states
“Code as law” is the (gatekeeper) concept that Internet design can be remade to help and achieve enforcement .
Examples of code as law include
• Geolocation: Requiring online businesses to tailor their offerings based on the location of the end user
• Blocking / Filtering: Attempting to stop end users from accessing material hosted abroad
• Digital Rights Management: Attempts to stop e.g. copying of DVDs
Implications of code as law (from a regulatory standpoint for Governments)
• Greater effectiveness
• Cheaper enforcement
• Prone to function creep
• Indirect and opaque
• Beyond legal redress
• Conceals state involvement
• Eliminates legal rights – for example content rights
• Eliminates feedback
Gatekeepers: A new mechanism to enforce regulation
Gatekeepers are asked to enforce a regulatory view – even when they do not have the legal mandate to do so – which raises the questions of Intermediary immunities. Intermediaries who act by Proxy seek immunities because inconsistent national laws fragment common markets and create fear of possible criminal or civil liability. For instance: Is the ISP subject to the same legal and practical constraints as the Post Office?
Intermediary immunity in turn raises more issues
• Uncertainty forces intermediaries to err on the side of caution. Uncertainty tends to force intermediaries to enter into “voluntary” self-regulatory schemes E.g. Eircom’s “three strikes” system.
Implications of gatekeeper regulation
• Minimizes enforcement / jurisdictional problems (Reduces enforcement costs, avoids need to track / identify users)
• Censorship by proxy (Imposing liability may chill expression, Incentives and accountability)
• Raising power of government at expense of parliament (laws)
• Avoids usual public law oversight (FOI / parliamentary scrutiny / judicial review)
Perceived advantages for governments
• Responsiveness
• Industry expertise
• Flexibility
• “Light touch” and low cost regulation
• Avoids need for legislative time
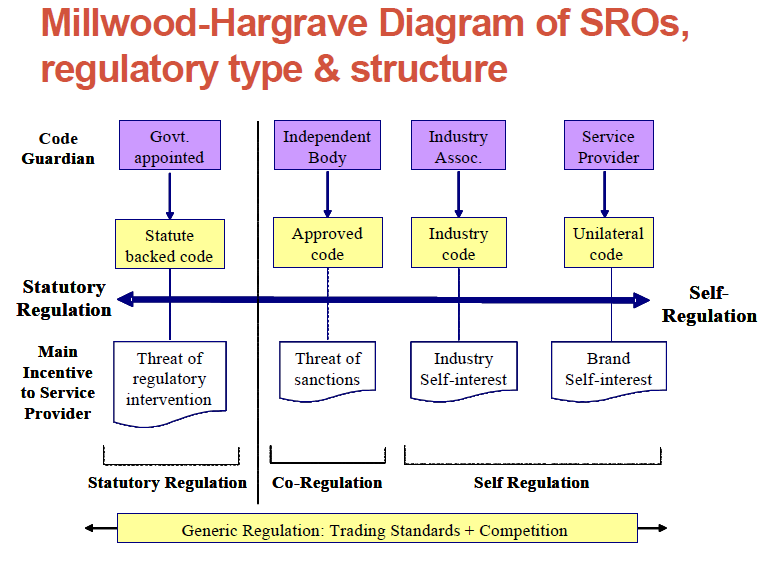
In addition, the talk made a reference to Milton Hargrave Diagram of SROs, regulatory type and structure which gives a wider picture: